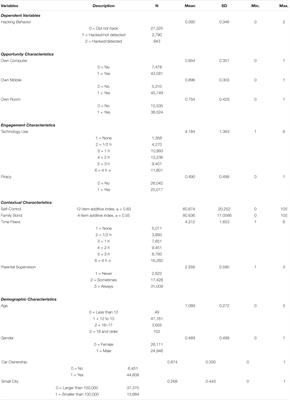
All your Ether are belong to us (a.k.a Hacking Ethereum-based DApps) - Luis Quispe Gonzales - YouTube

Hacking Communication to Prevent Identity-Based Violence: Civic Hacker Podcast Season 2 Episode 5 | Civic Hacker Network

Android for Hackers: How to Turn an Android Phone into a Hacking Device Without Root « Null Byte :: WonderHowTo