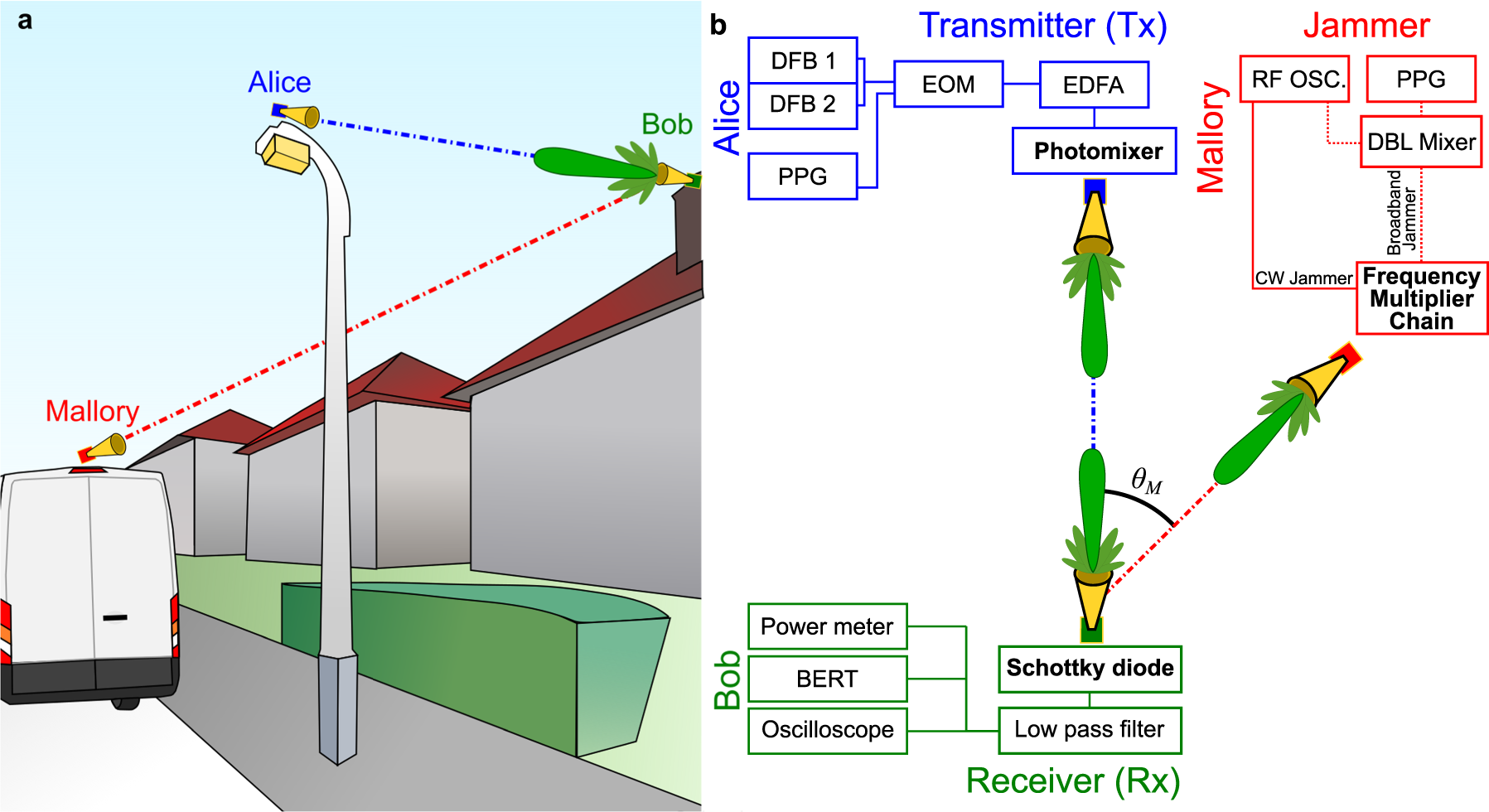
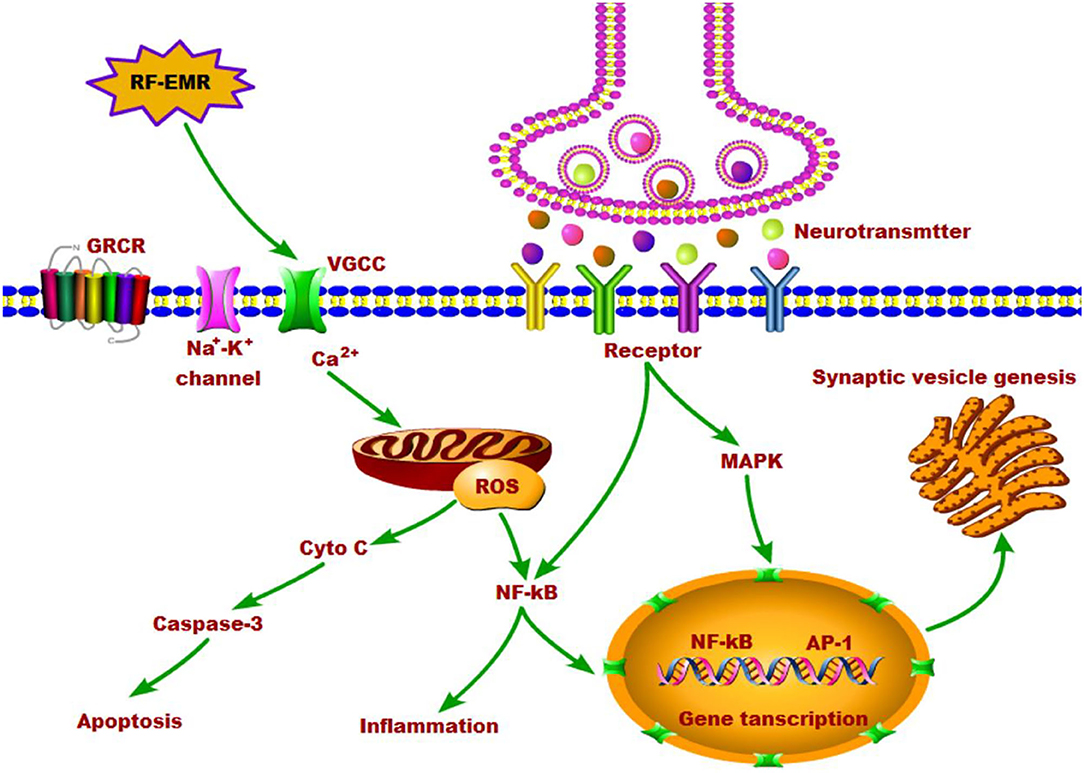
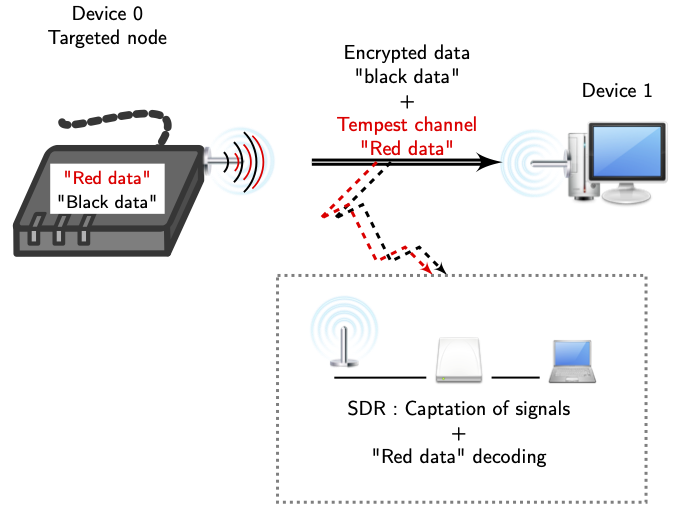
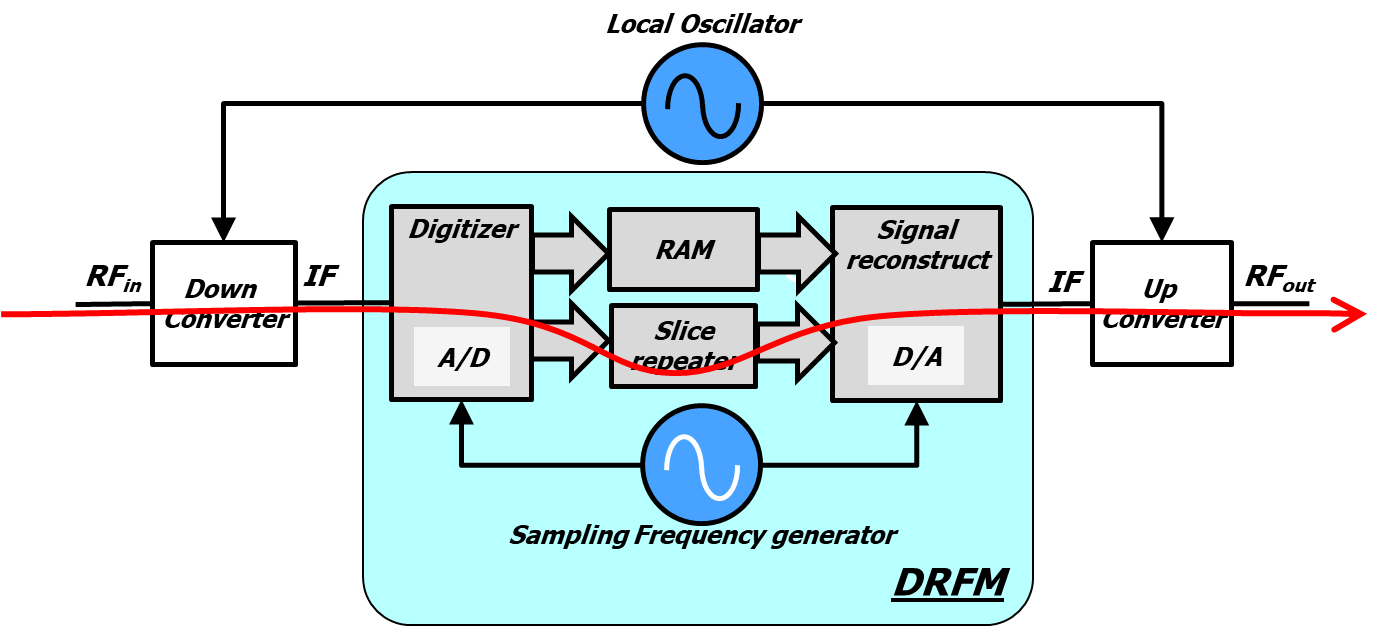
Applied Sciences | Free Full-Text | Detection of Primary User Emulation Attack Using the Differential Evolution Algorithm in Cognitive Radio Networks
Cardiac catheter ablation treatment Atrial fibrillation rhythm problem minimally invasive procedure attack cath lab treat Coronary x-ray Radio frequency Sinus Ventricular SVT ECG ICD Radiofrequency AV Stock Vector | Adobe Stock

Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News

Radio Frequency Operations and Training From a Virtually Different Point of View - United States Cybersecurity Magazine